A Case Study Based on a Global Financial Services Leader's Agile DevSecOps Journey
As digital systems grow more complex and security threats become more sophisticated, the pressure to deliver secure, high-quality products at speed has never been greater. Each day, countless digital products are being built amidst growing complexity and rising cyber threats, whilst the pressure to deliver changes faster has only intensified. According to Google DORA State of DevOps reports, top-performing teams deploy code much more frequently than the rest (sometimes multiple times per day, if needed) and with substantially fewer failures – DevSecOps allows them to do it as fast and successful as required by the demand of their users, security drivers, or other factors.
To keep up, more enterprises are turning to Agile DevSecOps. This approach brings architects, developers, test engineers, security teams, and operations together to build fast, build right, and build secure.
Tech Mahindra’s engineering transformation frameworks have enabled multiple global organizations to adopt Agile DevSecOps at scale, achieving faster time to market, improved code quality, and consistent governance. Below is a practical trail map to implementing Agile DevSecOps practices based on TechM’s extensive experience working with large enterprises across industries.
The Trailmap: From Containerization to “Everything as Code” to Cloud-First Engineering Paradigms
In this case, our journey to implement Agile DevSecOps practices started with adopting containers for CI/CD to create a foundation for migration from one application lifecycle management platform to another. Rather than pursuing siloed automation, Tech Mahindra recommends focusing from the very onset on a cross-functional rollout of these practices, enabling engineering, security, and operations teams to work collaboratively and design for operational excellence and future cloud cost effectiveness already at the early stages of the journey. The first major milestone was to move toward an "everything as code" approach, where all workloads, environments, policies, and infrastructure are version-controlled, automatically tested, and configurable. This unified strategy reduces risks associated with consistency and possible human error, among others, and sets the stage for further scalability.
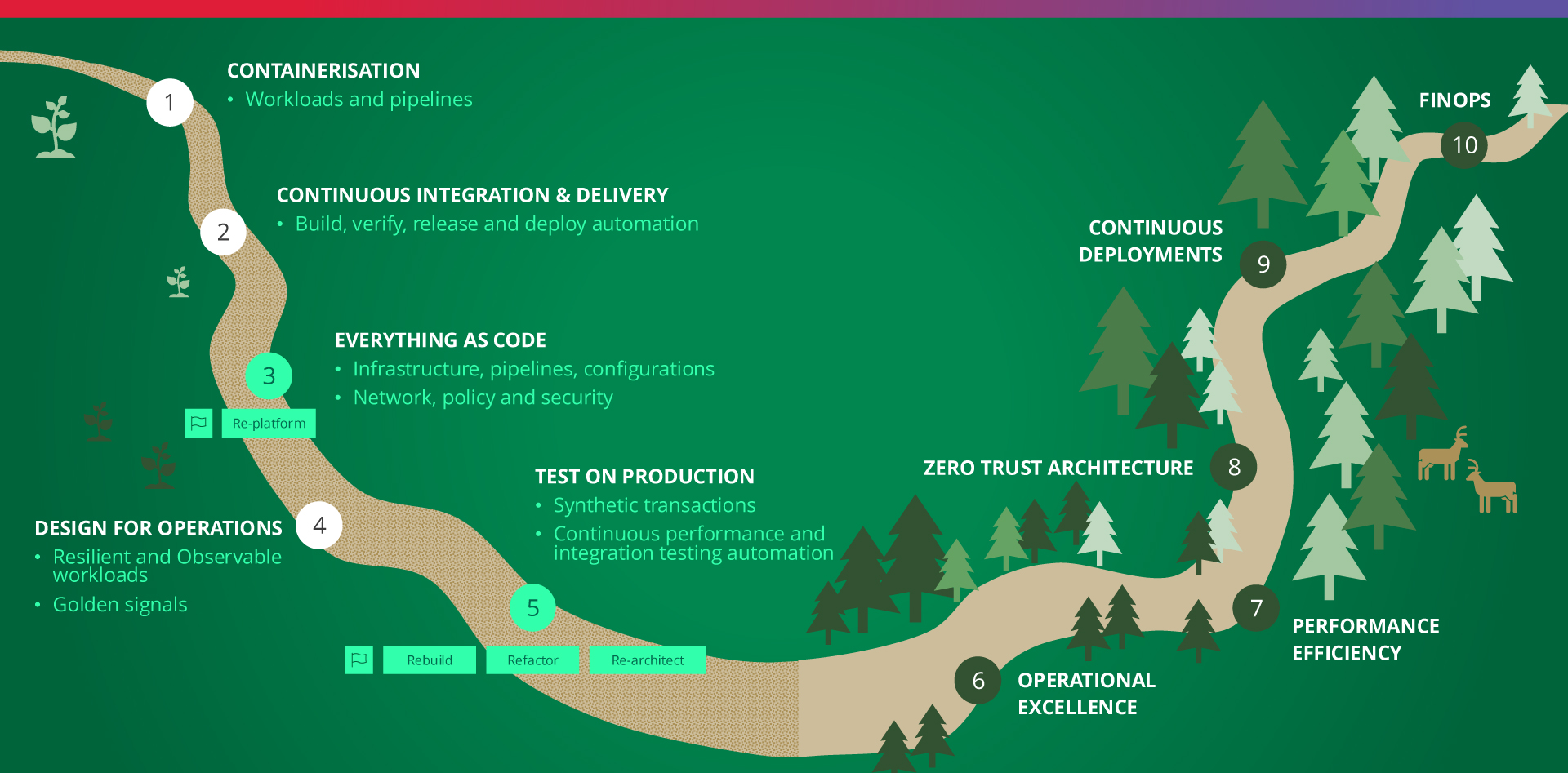
This stepwise approach works best when blended into a strategic landscape, processes, infrastructure, and tools transformation roadmap, integrating infrastructure and tools modernization with application modernization, aligning for a cohesive action toward a singular objective.
Early Cloud-Native Mindset: Future-Proofing Transformation
Organizations that embed cloud readiness and cloud-native thinking early in their journey are much better positioned to scale, modernize, and more easily leverage public cloud platforms, even if the public cloud journey is not high on the organization’s agenda for various reasons.
Hence, Tech Mahindra recommends anchoring transformation strategies using cloud-native principles from the outset. We recommend drawing inspiration from and aligning with industry-standard frameworks, such as those from the Cloud Native Computing Foundation (CNCF), to build scalable and future-ready systems. It also means leveraging public and internal assets, like reusable guidelines, design patterns, and reference architectures – e.g., the Well-Architected frameworks, available from Azure, AWS, and others, to accelerate delivery. Most importantly, both infrastructure and the engineering culture must be prepared to adopt the cloud, ensuring that teams and technologies are aligned for long-term success across the organization – more straight-forward ‘lift and shift’ type approaches can only work in a short term perspective as usually these lead to higher costs and no significant efficiency gains one would usually expect to obtain with the switch to a modern hyperscaler instead of more traditional infrastructure or a self-hosted private cloud.
Insights from Industry Engagements
Drawing on its work with large enterprises across verticals, Tech Mahindra offers the following insights for successful Agile DevSecOps integration:
- There is a limit to what you can achieve with old (monolith type) applications in the state of DevOps, e.g., deployment frequency, fully automated infrastructure provisioning, zero trust architecture, etc. – re-architecture and redesign will be required for parts of the landscape.
- Accelerating DevOps is a journey, and the sequence is essential. Some milestones cannot be achieved before others.
- While you must go through this journey with different assets progressing through the trail map at their own pace, it's essential to consider the future requirements of the later stages, such as cloud cost efficiency, from the beginning. Otherwise, the commercial net impact could be low or negative once public cloud bills add up.
DevSecOps: Culture Over Tools
To enable successful DevSecOps adoption and engrain it into the organization's engineering culture, the practices are not less important than the tools, and implementing them within the organization is a journey, not a one-off exercise.
Although automation can assist greatly, simply automating your CI/CD pipelines and tests alone won’t be sufficient. Instead, you should equip each step of your DevOps workflow with the required practices, policies, and controls.
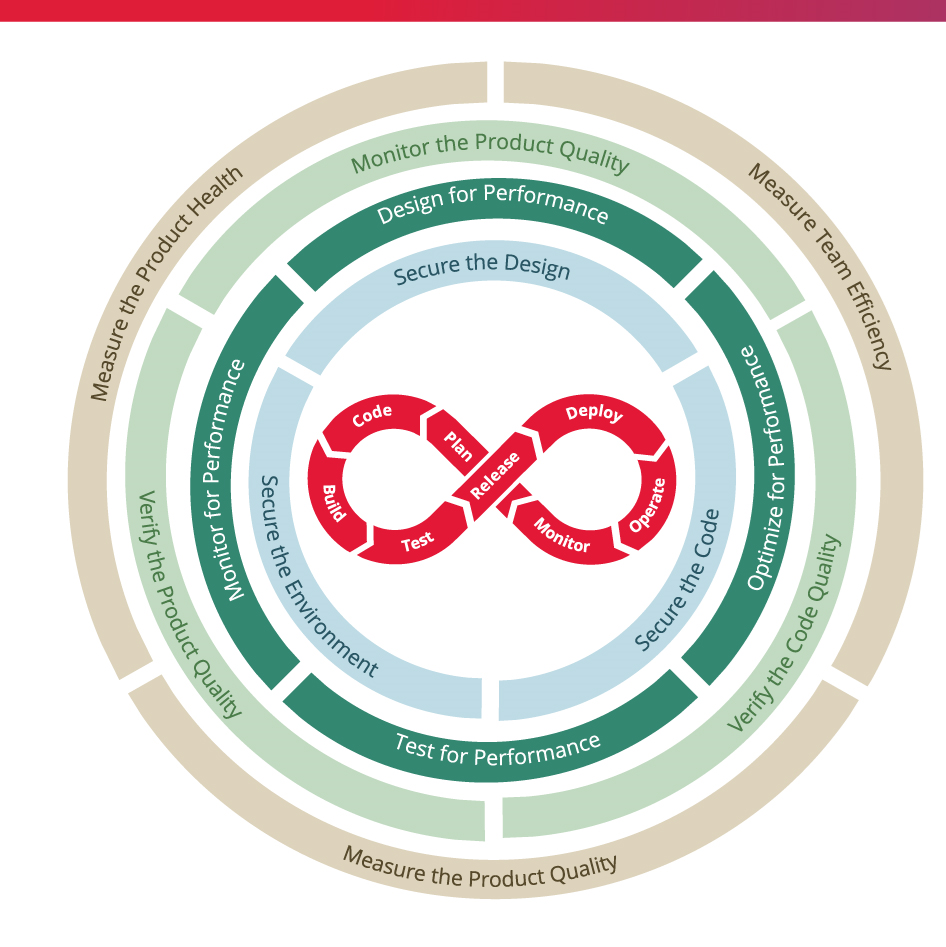
Security Controls
Integrate security natively in the DevOps process - each stage of a continuous integration and continuous delivery (CI/CD) is equipped with security controls to:
- Secure the Design
- Secure the Code
- Secure the Environment
Performance Controls
- Continuous performance focus on how to meet the requirements and maintain performance efficiency as demand changes and technologies evolve
Quality Controls
- Integrate quality controls in the DevOps process to meet product functional and non-functional quality requirements
- Verify code quality and product quality characteristics at each stage of a continuous integration and continuous delivery (CI/CD) DevOps process
Metrics
- Continuously measure quality characteristics against defined baseline (metrics) at each stage of a continuous integration and continuous delivery (CI/CD) DevOps process
Specific security controls, such as static code analysis and runtime vulnerability scanning, are obvious candidates for automation and integration directly into the CI/CD mechanics. However, it is essential to note that not all controls need to be automated from the outset. Practices are more important than the tools – e.g., having a code analysis or vulnerability scanner can be rendered useless if the teams do not pay enough attention to the output of these tools and don’t prioritize findings high enough in their backlog to be addressed in a reasonable time. Peer reviews through pull requests are a great example of a valuable practice that isn’t automated (though, with the rise of GenAI, we observe significant potential and are seeing good tangible results for intelligent automation or, as a minimum, AI augmentation of these processes as well).
Designing for Multi-Dimensional Quality
Tech Mahindra’s DevSecOps model encompasses four pillars that guide tool selection, practices, and engineering workflows:
- Security by Design – focusing on the design of the solution, workload, and the environment.
- Performance by Design – Including various approaches for preemptive observability, benchmark testing, and performance/load measurement during multiple application lifecycle stages.
- Shift-Left Quality Assurance—Defects are resolved sooner through early automated testing embedded in continuous integration, ensuring smart but sufficient code coverage, using test-driven development methods, and consistently monitoring product quality throughout different stages of the lifecycle.
- Agile Metrics and Operational Health – e.g., team velocity, defect leakage, and other lean and agile metrics to continuously assess and measure how team efficiency and product quality are evolving.
With an adapted, curated toolkit for every client-specific environment, these pillars guide the tooling decisions and how engineering teams operate, collaborate, and improve over time. However, the tools are less necessary than the right mindset and practices: one non-negotiable is the right blend of engineering culture that fosters security, quality, and efficiency as a function of all the teams in line with the Agile DevSecOps model.
Final Thoughts: DevSecOps is a Continuous Journey
Setting up Agile DevSecOps is not as simple as implementing a toolchain. Instead, it is a journey that must be undertaken through hands-on, multi-faceted teamwork and clear vision and support from both within and outside a particular team. The march could be protracted, and resources could shift at different rates. Still, with a definite path and a solid cultural underpinning, eventual agility is not an option—it is a given outcome, provided that the organization stays persistent on its journey towards this aspirational goal.